Books
-
 Understanding the Linux Kernel
Understanding the Linux Kernel
-
 Linux Administration Handbook
Linux Administration Handbook
-
 Linux Server Hacks, Volume Two
Linux Server Hacks, Volume Two
-
 Linux Server Hacks: 100 Tips & Tools
Linux Server Hacks: 100 Tips & Tools
-
 Learning the vi and Vim Editors
Learning the vi and Vim Editors
-
 Security Engineering
Security Engineering
-
 Nmap Network Scanning
Nmap Network Scanning
-
 The Art of Deception
The Art of Deception
-
 The Art of Intrusion
The Art of Intrusion
-
 Secrets & Lies
Secrets & Lies
-
 Advanced C Programming by Example
Advanced C Programming by Example
-
 Effective C++: 55 Specific Ways to Improve
Effective C++: 55 Specific Ways to Improve
-
 Effective STL: 50 Specific Ways to Improve
Effective STL: 50 Specific Ways to Improve
-
 Python Essential Reference
Python Essential Reference
-
 Design Patterns
Design Patterns
-
 TCP/IP Illustrated Volume I
TCP/IP Illustrated Volume I
-
 Advanced Programming in the UNIX
Advanced Programming in the UNIX
-
 Hands-On Machine Learning with Scikit-Learn and TensorFlow
Hands-On Machine Learning with Scikit-Learn and TensorFlow
-
 Modern Information Retrieval
Modern Information Retrieval
-
 Ta Eis Eauton
Ta Eis Eauton
-
 The Game
The Game
-
 Keys to Great Writing
Keys to Great Writing
-
 The Happiness Hypothesis
The Happiness Hypothesis
-
 Quiet
Quiet
Whitepapers
- When agile fails, a hotfix is not enough (Sep 2013)
- QAWeb - Using Django via SSH for QA Statistics (Aug 2012)
- IPP - Launching a new prototype into the market (May 2010)
- On the Way of Making Data Disappearing (Dec 2009)
- An Information Security Policy for the Faculty of Science (FNWI) (Nov 2009)
- The Security features of NetCents micro-payment protocol (Apr 2009)
- PKC on RFID tags: A survey on the GPS identification scheme (Apr 2009)
- Differential Fault Analysis on Smart Cards using Elliptic Curve Cryptography (Mar 2009)
- An Overview of Certificate Request Message Format (Feb 2009)
- A Survey on Ear Recognition (Feb 2009)
- SELinux in a Health Information System (Feb 2009)
- Security Service Granularity (Dec 2008)
- Wardriving - Building A Yagi Pringles Antenna (Oct 2008)
Photography
5th December 2024
Office III
After several years of remote work, I’ve been focused on redesigning my home office to maximize productivity. A DIY standing desk, utilizing a MAIDeSITe dual-motor adjustable frame to ensure it could easily support my two monitors. For the surface, a custom-built tabletop, with a warm walnut finish. To complement this setup, I created a custom wall-mounted whiteboard using an IKEA white glass tabletop. I paired it with a small IKEA shelf to keep my markers organized and mounted it right beside my desk.


15th April 2012
Office II


31st March 2011
Office I

25th October 2021
ThinkPad T14s
My experience with the ThinkPad T430 was nothing short of outstanding. For nearly a decade, it served as my primary workstation and remains the most durable device I have ever owned. Recently, I decided to transition to the T14s in search of a lighter, more portable form factor. While I’ve made a slight shift by opting for the AMD Ryzen 5 processor, I’m pleased that the legendary keyboard experience remains the same. Only time will tell if this new model can match the remarkable longevity of the T430.

30th December 2017
7-years non-stop, time for a server upgrade!
The idea of a server setup started around 2010. Since that time, the server changed multiple physical locations and countries, but never stopped running and serving my needs. It became a habit and one of the greatest ideas I had for getting a playground for experimentation and independence. It allowed me to deliver and maintain core projects such as teacherfinder.gr, hireme.gr, but also hundreds of others which helped me to grow as a software engineer. Of course, it would not be fun, if I did not include also a RGB Fan Controller for voltage, temperature and RPMs.


10th August 2013
ThinkPad T430
After almost 5 years, I decided to switch from a Macbook to the ThinkPad T430 & install what else, Debian. Quite powerful, very solid, amazing keyboard and with a battery that last for hours.

24th October 2011
Diamond BVU195
The last week I was looking for a device that will allow me to connect a second monitor at my macbook. After a bit of investigation I ordered the Diamond BVU195, which is a usb adapter that outputs the desired DVI connection. After downloading and installing the required drivers, my 2 monitor setup was ready. Tiger, Leopard & Snow are supported from a stable version and there is a beta one for Lion, which I did not test yet. Overall, I would recommend the BVU195, as a relatively cheap solution. However, keep always in mind that you will be left only with one usb port available (but worth the pain, all the way…).
1st April 2011
Server Build
I always wanted to build a server that would have a fancy “see through” look. Below are some photos from the final build. The CPU capabilities, powered by Intel i7.


28th December 2025
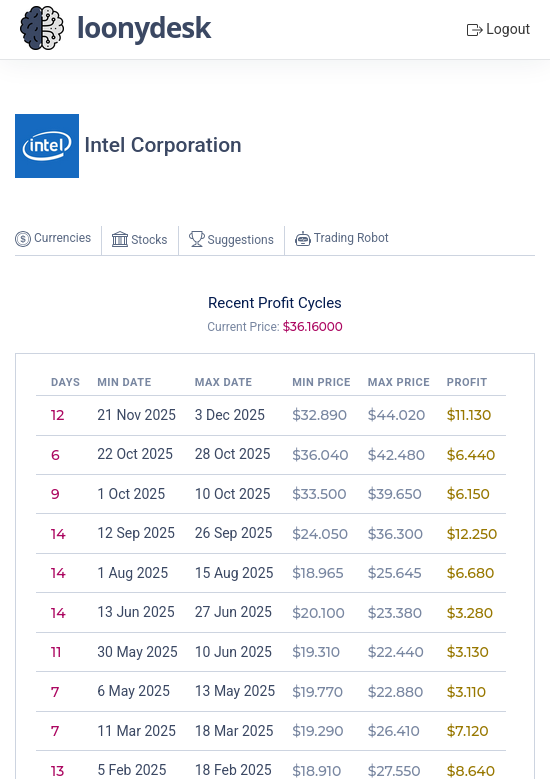
Trading Robot
[Stock and Currencies]
Under the master loonydesk.com domain, there is a new tool to analyze daily stock and cryptocurrency prices. It simulates positions using a developed trading robot. The main idea is to detect profit cylces based on the past behavior and try to make better predictions.
8th November 2021
HandCrafted Epoxy Resin River Table
I could not find a coffee table that I like enough to put in my living room. While searching, I came across the idea of Epoxy Resin River Table (DIY). I was hooked. I had to try to build it. Here are my results:







16th January 2018
DataGrinder
It is clear that as the volume of data keeps increasing, internal tools that will help you build a better subscription business model, are required. You have to be able to use all the data that you have in order to understand your customers and grow your business. That’s what DataGrinder is all about. A custom internal tool for data mining.
12th December 2017
Launching HireMe
This project aims to expand the idea of teacherfinder.gr into a broader scope search engine for all freelancers.

5th August 2010
Building a Diskless Cluster
As my internship reaches to an end, I would like to thank Intel for hosting the dissertation for my master degree. During my stay here in Shannon, I found many new innovative directions that could be explored and I had the chance to extend/reveal my skills. Inspired from the field of computer security, with obvious influences from the area of cryptography, I discovered a personal paradise at Intel’s Lab.
In a nutshell, I built a multi-node diskless cluster that is controlled from a main board and it is able to schedule jobs in parallel. The interesting part comes from the fact that the entire approach is diskless and it shares only a single shared storage point, located at the main board. That in practice means that every processing on the nodes is done on the fly through the network and apparently the operating system is also loaded on the fly by using the Pre-Boot eXecution Environment (PXE) & Tftpboot.
The idea behind the cluster was to explore the processing that we could obtain for general hashing operations. There are many open source tools for High Performance Computing and I was more than glad to explore thi. Intel Shannon, significantly contributed to the entire project, since it provided me with all the necessary hardware toys and a high-tech lab to setup my systi. I would like to personally thank the following people: Benne de Weger, Padraic Garvey, Michael Hennessey, Pierre Laurent, Sergio Borghese and Joseph Gasparakis.
Document: A Diskless Cluster Architecture for Hashing Operations
Slides: A Diskless Cluster Architecture for Hashing Operations (Pres)


27th December 2025
TeacherFinder
Launched in 2010, this project started as an exploration into Python and Django v1.3. It has continued to grow and adapt over the years, incorporating new tech stacks and improving.




30th December 2022
TeacherFinder
[Another update]
TeacherFinder got another major update and some exciting new features. It’s almost 12 years and the journey continues …
27th April 2020
TeacherFinder
[What a Journey]
Almost a decade for TeacherFinder. Another major upgrade that aims to offer the best possible experience and usage to users.
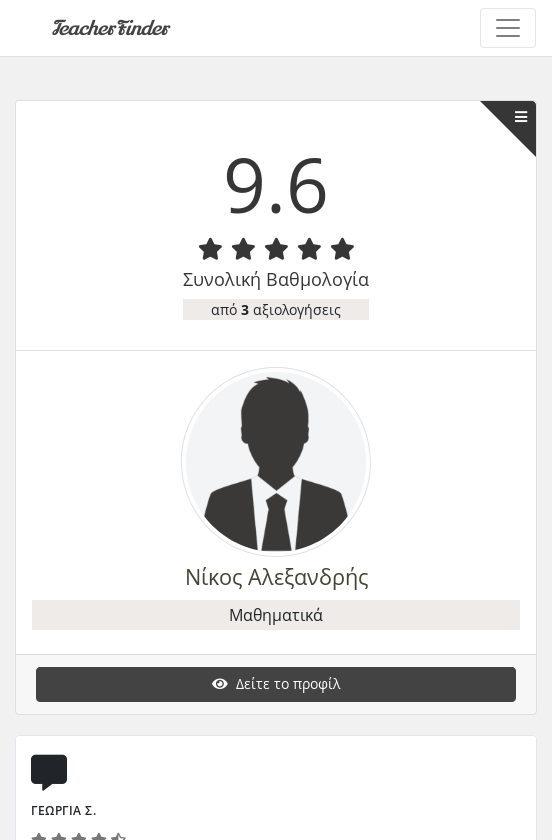
2nd February 2016
TeacherFinder
[The Major Update]
It’s been a while, but the new fully upgraded version of TeacherFinder has been published. A lot of new features, enjoy!

5th August 2013
TeacherFinder
[The Facelift]
Recently, I was working on facelifting TeacherFinder. Tonight, I uploaded the new version which includes a better look & feel, together with some updated features for the search engine.

The majority of the changes were focused on optimizing the respond time for the requested queries. The searches are now performed a little bit faster, making searching on TF much easier. Finally, the visibility for classified ads was further improved and a number of statistics with regards to the TF visitors became available.
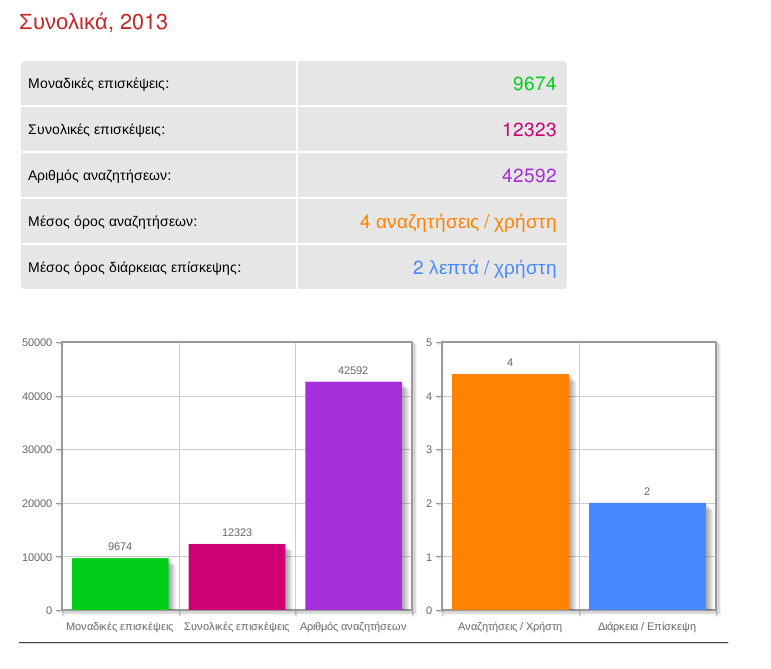
28th February 2012
TeacherFinder
[Goes International]
TeacherFinder goes international! The team of TeacherFinder will continue developing additional features, targeting to create the best user experience possible.
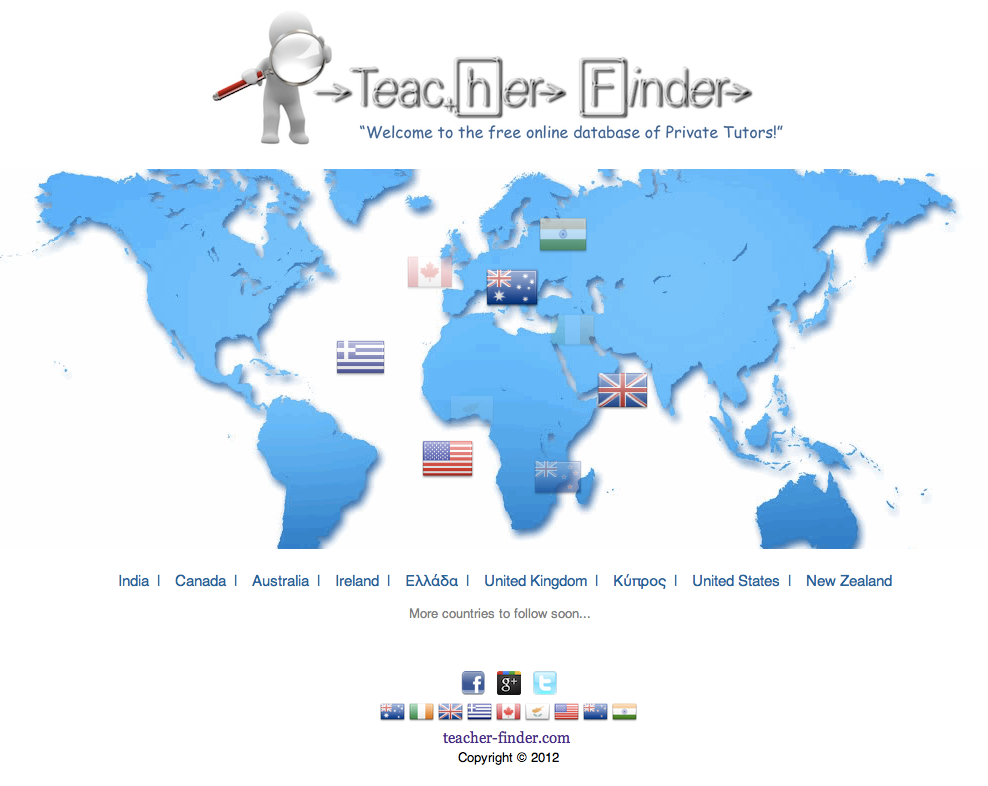
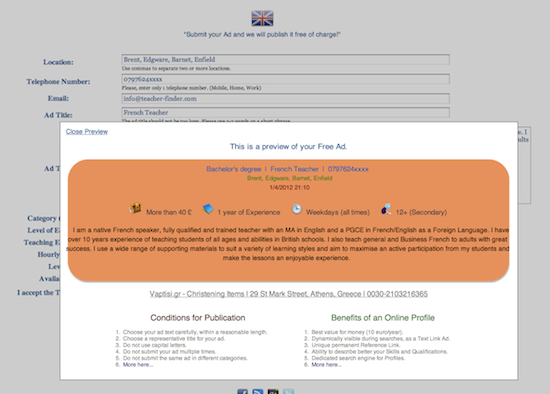

15th January 2012
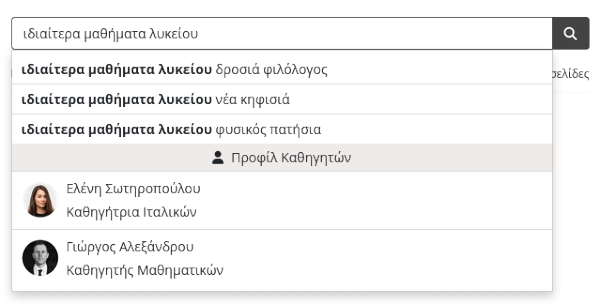
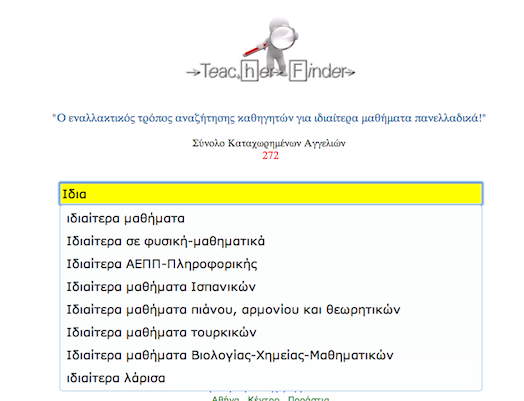
TeacherFinder
[A Better Search]
A useful autocomplete feature was added today at the searching capabilities of TeacherFinder. The autocomplete look is as follows…
26th December 2011
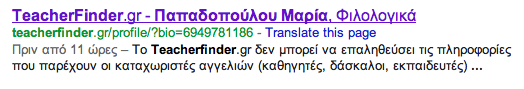
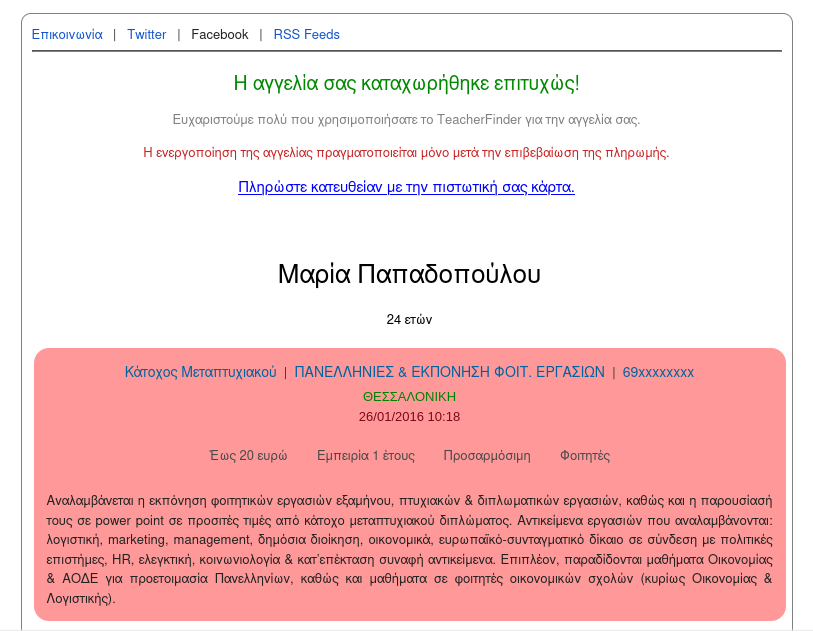
TeacherFinder
[Online Profiles]
From now on, the users of TeacherFinder will be able to submit their own personal profile for one year, at a very low cost. Below, how the profile looks like, when crawled by Google Engine.
4th November 2011
TeacherFinder
[Initial Launch]
After almost one month of coding every single evening after work, the new platform for finding private teachers in Greece was launched last night.
Totally re-factored and with a fresh new look, is hoping to serve the best possible way its users. It is offered completely free and it adopts a post-it like appearance with different colors for each category.
The intention is to continue developing new features for the platform and extend the functionality that already offers. However, it is mainly a hobby for me and thus, there are no guarantees for future deliverables.
9th April 2017
The Marathoner’s Metaphor
A professional marathon athlete is hired from a team in order to run in a big national event in Dublin. He arrives in Cork 5-days before the event. For the first time after hired, he is told that in order to reach Dublin, he is not allowed to use any transportation (train, airplane, bus, etc.), but he has to walk from Cork to Dublin. Of course, he is unpleasantly surprised.
The marathoner understands that even if he walks 30 miles per day, he might cover the 150 miles on time, but then he will have to run 40 km of a marathon and compete against all the other athletes. He then asks whether he can use a bicycle, as that it will save him time, allowing him to do 75 miles per day and reach Dublin in 2-days, rest 3-days and race. Yes, he can use a bicycle, but he has to order the bicycle and wait minimum 3-days to get it and spend another 1-day to register the bicycle and insure himself for travel injuries. Now, he realizes that he has 1-day to do 150 miles with a bicycle and then run the 40 km of the marathon.
[marathoner] → But I will have to run a marathon with brand-new shoes ?
[team] → Yes, what’s the problem ?
[marathoner] → Sure I understand ...
The marathoner hangs up the phone. The mental game has already started inside his mind, but he is not even racing. His initial goal was to compete for the win, but the only thing he thinks now is whether he will even be able to finish the race. Obviously, the marathoner is already confused and psychologically stressed. He decides to stop for food and water in one of the petrol stations. An hour later, as the marathoner leaves the petrol station, his phone rings. Marathoner’s best friend, also a professional marathoner is on the phone.
[friend] → Hey, where are you ?
[friend] → Are you already in Dublin resting for the upcoming race ?
The 2 friends have been training for years together and run several times in long distance races side-by-side. The marathoner explains the situation to his friend and the reasons that he is not in Dublin yet. Phoneline silence, a few seconds later, only a single question:
[friend] → Why do you waste your talent, after so many years of hard work and dedication ?
[friend] → We both know, you won’t be able to even stand in that race, not have a chance of winning.
The marathoner thanks his best friend for the moment of clarity and he finds a B&B to spend the night. The next day, he calls the team owners to say that he wants to have a transportation to Dublin, otherwise he cannot race. The owners reply that it is not possible and the only thing that he should target as goal is to just register for the marathon the day of the race, and run even for 1-minute, otherwise the owners will lose their sponsorship. The marathoner explains that his intention was to race for the win and not only the participation and he will quit if he cannot reach Dublin a few days before the race, in order to rest. The owners suggest to the marathoner to start running instead of walking until he reaches Dublin and wear also his own pair of sports shoes in order to get used of them, as this is his best alternative option for the race. He will arrive in Dublin 1-day earlier from the race and solve also the problem of the shoes. The marathoner quits the next day.
13th September 2015
When agile fails, a hotfix is not enough
It is incredibly confusing how sometimes companies try to apply Agile Development and how they terribly fail to do so. There is no comprehension of what they define as their “own agile development” and certainly the chosen structure is at best unstable. The following document analyses the situation with a pure engineering insight, leaving out of the picture all the micro and macro management processes. Finally,it challenges the fixed model that exists in most of the companies, which sets: “Agile development as the one and only panacea for everybody to follow”. In that attempt, it proposes the Manager, Architect and Developers (MAD) model, purely inspired from different aspects of real life examples.
Document: When agile fails, a hotfix is not enough
































































































































































